Maximizing Business Security: The Ultimate Overview to Electronic Security Solutions
In the hectic and ever-evolving landscape of business security, the dependence on electronic security options has become critical for safeguarding beneficial possessions, confidential details, and preserving operational connection. In this guide to digital safety solutions, we will certainly explore the latest fads, innovative technologies, and ideal practices to fortify your organization against potential risks and vulnerabilities.
Importance of Electronic Protection Solutions
When thinking about the security of assets and delicate information, the importance of electronic safety and security services can not be overemphasized. In today's interconnected world, where cyber dangers are constantly progressing and becoming a lot more sophisticated, services have to prioritize executing durable digital safety and security measures to protect their information and procedures. Digital security options encompass a wide variety of modern technologies and practices developed to resist unapproved access, data breaches, malware, and other cyber dangers.
Among the key benefits of digital protection services is their capability to give real-time surveillance and danger discovery. BQT Solutions. Through tools like intrusion detection systems, firewalls, and security information and event management (SIEM) systems, organizations can proactively identify and reply to safety and security events before they escalate into major violations. In addition, digital safety and security services help make certain conformity with market policies and criteria, protecting businesses from potential lawful and monetary effects
Kinds of Electronic Safety Systems
Offered the important significance of digital security solutions in securing companies versus cyber risks, it is important to discover the numerous sorts of digital security systems available to enhance protection and strength. One of the most usual sorts of digital safety and security systems is the firewall software, which works as an obstacle in between a company's inner network and external networks, filtering out potentially harmful data. Invasion Detection Equipment (IDS) are additionally vital, as they keep an eye on network web traffic for suspicious task and alert managers to possible risks. Additionally, services often depend on encryption modern technologies to safeguard sensitive information both at remainder and in transportation. Gain access to control systems, consisting of biometric readers and keycard accessibility, aid control access to physical rooms and safeguard properties. Video surveillance systems play a function in surveillance and recording tasks within and around the properties. By employing a mix of these electronic safety and security systems, services can develop a durable protection versus various safety hazards.
Carrying Out Gain Access To Control Steps

Additionally, gain access to control procedures can be integrated with monitoring systems to check and tape people' activities within secured areas. This combination boosts protection by offering a thorough overview of who is accessing particular places at any type of offered time. Furthermore, gain access to control systems can be set up to limit accessibility based upon time, area, or individual credentials, allowing services to personalize protection methods according to their details demands.
Cybersecurity Best Practices
To enhance overall security position, executing robust cybersecurity best practices is crucial in guarding electronic properties and information stability. One fundamental practice is ensuring normal software program updates across all gadgets and systems to patch vulnerabilities promptly. Using strong, unique passwords and applying multi-factor authentication includes layers of protection against unapproved gain access to. Conducting regular protection audits and assessments aids determine weaknesses and locations for enhancement. Employee training on cybersecurity understanding is vital in stopping social engineering strikes and guaranteeing a security-conscious labor force.
Developing an extensive case response plan makes it possible for swift and efficient responses to safety violations, reducing prospective damages. Encrypting sensitive information both in transit and at remainder provides an extra obstacle against information violations. Carrying out access controls based on the principle of the very least privilege limits the direct exposure of important systems and information to only those that need it for their duties. Regular backups of data guarantee that in case of a ransomware attack or data loss, essential information can be recovered. Embracing a positive method to cybersecurity through continual monitoring and hazard intelligence aids spot and reduce prospective dangers before they intensify. By integrating these finest techniques into cybersecurity strategies, companies can fortify their defenses against developing cyber risks.
Security and Surveillance Solutions
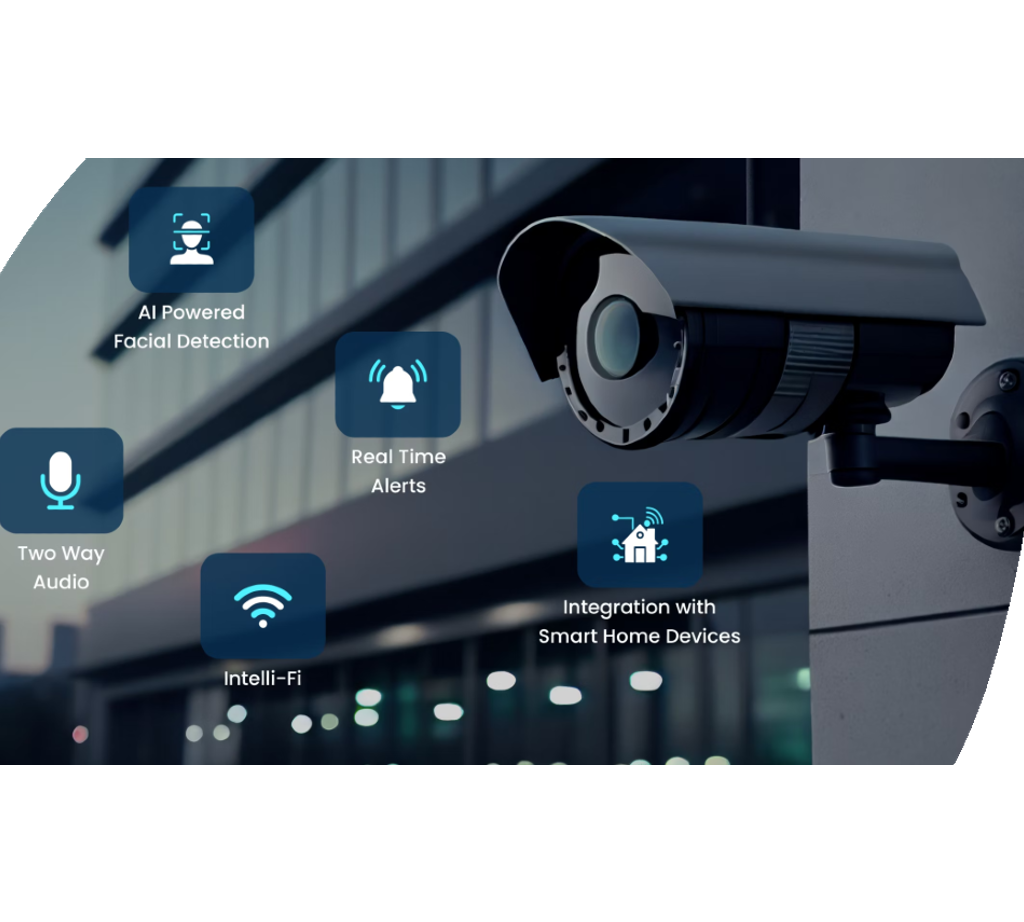
Video clip monitoring options offer remote tracking capabilities, enabling accredited personnel to watch on the properties also when off-site. Additionally, advanced features like movement discovery, face recognition, and permit plate acknowledgment boost the total safety and security posture of the organization. Integrating monitoring systems with alarm and access control even more reinforces the safety facilities, making it possible for an aggressive reaction to possible protection breaches.
Verdict
In conclusion, digital protection options are vital for making best use of organization security. i was reading this It is essential to invest in the appropriate digital safety and security systems to make certain the security and safety and security of the organization.